With the digitization of healthcare, day-to-day healthcare services have come from paper to electric and mobile devices, collecting and storing every aspect of healthcare data. Healthcare data has become the driving force behind optimizing and improving healthcare services. Every day, healthcare organizations worldwide face the never-ending responsibility of protecting patient data and private communications. Meanwhile, modernization, scalability, and increased remote healthcare accessibility are expanding the need to secure healthcare data.
Cloud security in healthcare is more than just a technical term; it’s about public confidence and safety. Additionally, ensuring cloud security for healthcare is crucial to expanding healthcare services globally and being compliant with state regulations and compliance requirements. According to the Cloud Security Report, around 76% of enterprises are deeply concerned about cloud security, and almost 59% of executives view misconfigurations as a threat. Healthcare cloud security ensures data protection following the best practices. This blog will cover the best strategies for securing healthcare data with the cloud.
What is Cloud Security in Healthcare?
Cloud security in healthcare ensures data privacy across applications, infrastructure, and platforms. It also offers the confidentiality and integrity of patient records, clinical applications, and valuable medical data. Indeed, cloud security is currently one of the major concerns in healthcare.
Breaches and data loss can seriously impact healthcare organizations and patients. From the patient’s perspective, their data, which includes health conditions, medical information, and transaction records, is extremely sensitive. Any breach of this data, no matter how modest, can violate patient privacy and result in financial loss or ransomware attacks.
Furthermore, healthcare cloud security is critical for creating confidence between physicians and patients, which impacts healthcare facilities’ reputations and market positions. Given the rigorous and complicated standards governing healthcare data privacy, even a tiny violation can result in huge fines and losses for the organization. Cloud security in healthcare takes care of sensitive data and makes sure that healthcare operations remain streamlined without compromising.
Read this blog to know about the- Impact of Cloud Computing in Transforming the Healthcare Industry
Security Challenges in Healthcare
The whole world operates on data, and healthcare is not untouched by it. With the introduction of digital record keeping and the integration of advanced technologies like IoT, AI, and ML, the healthcare industry has boomed with data and its applications. However, with such enormous data come significant challenges, but they can be solved by healthcare cloud security solutions. Let’s understand some of the biggest challenges of data security in healthcare:
-
Encryption
Data protection via encryption is crucial to ensuring data security in the healthcare industry.
With the digitization of medical records and the exchange of sensitive information, robust encryption techniques are critical to protect data from unauthorized access. Encryption transforms data into a code that can only be deciphered with a cryptographic key, adding an extra layer of security.
Encryption can be complex and expensive, and ensuring interoperability between systems can take time and effort. However, healthcare cloud security solutions can help your business implement encryption to protect your data. Healthcare businesses must implement strong data protection policies and processes to avoid data breaches and unauthorized disclosures. Cloud security in healthcare enforces access rules, conducts frequent security audits, and implements zero-trust security.
-
Lack of Cybersecurity Awareness
One of healthcare’s most serious data security challenges is the need for cybersecurity education for healthcare practitioners. It’s a big challenge, possibly more than most people realize. Many healthcare professionals need appropriate training or education on protecting sensitive patient information from cyber threats. This exposes them to phishing scams, malware attacks, and other cyber-attacks that may jeopardize patient information.
To overcome this issue, healthcare institutions should engage their employees in comprehensive cybersecurity training. Organizations can significantly minimize the risk of data breaches and preserve patient privacy by educating healthcare providers on healthcare cloud security best practices and providing them with the information and skills necessary to recognize and respond to possible cyber threats.
-
Mishandling of Data
Healthcare providers are accountable for protecting and securing patients’ sensitive information, including medical history, personal information, and financial records. This data has the potential to be mismanaged due to unauthorized access, insufficient encryption, or poor storage methods, which can put the patients’ personal information at risk of being hacked.
Healthcare institutions must implement rigorous policies to solve this difficulty and teach their staff about safe data handling methods. Healthcare cloud security solutions enable access restrictions, encryption technologies, and periodic monitoring of systems for vulnerabilities, which are critical to protecting patient data and ensuring compliance with privacy rules.
-
Interconnected Healthcare Systems
The healthcare systems are being interconnected now with the adaptation of modern technology poses a significant risk to data security in the business. As healthcare technology progresses, the dependence on electronic health records (EHRs) and other digital platforms to store and share patient data grows. While interconnectivity has certain benefits, such as greater care coordination and easier access to patient data, it also poses substantial security vulnerabilities.
A breach or unauthorized access to one system can jeopardize the entire network, putting sensitive patient data at risk. To solve this issue, healthcare institutions must prioritize robust healthcare cloud security solutions such as encryption, strong authentication methods, and frequent security audits to protect patient data and ensure the privacy and integrity of their systems.
Read this blog to know about- AWS Cost Optimization: Strategies for Maximizing Cloud Efficiency
6 Strategies to Protect Your Healthcare Data
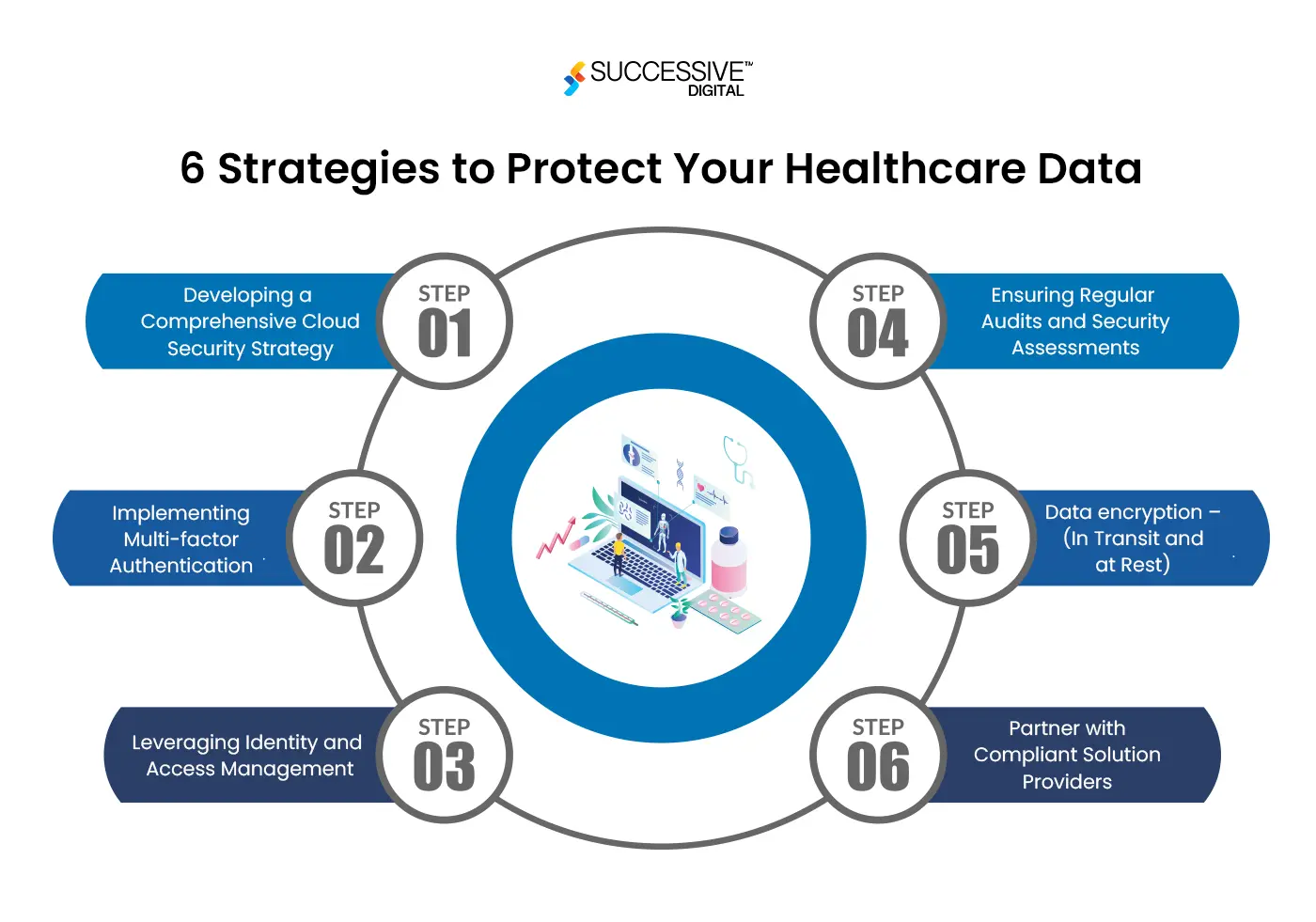
If best practices are followed, sensitive data will remain safe. When the security of sensitive data like healthcare data is at stake, it requires much attention. Here are five ways to protect your healthcare data:
-
Developing a Comprehensive Cloud Security Strategy
Developing a well-thought-out security strategy is critical in all situations and for all businesses. A reliable cloud consulting company can help you curate a comprehensive cloud security strategy. Risk assessment should be the initial step in identifying vulnerabilities particular to your organization. Aside from technical issues, human errors can also contribute to security breaches. Healthcare cloud security solutions help you identify the possible threats, and create a solution for the same.
Regulatory compliance is another essential component of a successful approach. HIPAA, GDPR, and other related data storage and transmission rules must be integrated into healthcare cloud security.
-
Implementing Multi-factor Authentication (MFA)
Multi-factor Authentication (MFA) is an excellent practice in healthcare cloud computing. Traditional login credentials are no longer practical against advanced and complex intrusions. MFA can solve this and improve security by requiring multiple verification methods. To gain access to your system, you must validate it using your mobile device, fingerprint, or facial scan in addition to a password.
MFA reduces the likelihood of unauthorized access, even if your password is compromised. For example, after entering a password, you may receive a text with a verification number or be prompted to prove your identity using biometric data such as a fingerprint. It prevents thieves from gaining access to your system or data.
-
Leveraging Identity and Access Management (IAM)
At its essence, IAM manages who has access to what in your cloud-based healthcare system. It’s similar to a digital ID card in that it not only verifies your identity but also specifies what you can do once in the system.
Furthermore, IAM enables healthcare businesses to build access controls based on job roles, limiting staff to only the data required for their specialized tasks. For example, a doctor can access patients’ medical records but not their financial information. Such an approach efficiently mitigates cloud security concerns for healthcare businesses while reducing the danger of internal threats, whether inadvertent or thoughtful.
-
Ensuring Regular Audits and Security Assessments
Routine checks of your cloud infrastructure will provide a complete snapshot of your current security posture, exposing risks you may be unaware of. It could be due to old software, ineffective access management, or insufficient data encryption. Scrutinous audits of your cloud infrastructure, data flow, access controls, and organizational security culture will assist you in identifying vulnerabilities before they are exploited.
Regular audits in your healthcare cloud security strategy provide twofold benefits. They keep your organization compliant with regulatory obligations while delivering actionable data to help you continuously enhance security procedures.
-
Data encryption – (In Transit and at Rest)
Encrypting data remains one of the most effective ways to protect data and secure healthcare companies. Encrypting data in transit and at rest is critical because it prevents attackers from decrypting patient information, regardless of whether they can access it. HIPAA compliance advises encrypting data but does not require healthcare institutions to do so. For encryption, the HIPAA rule allows healthcare providers and business associates to choose the encryption technologies they want to utilize and other measures that will accommodate the organization’s workflow and other requirements. Healthcare cloud security solutions enable robust encryption to secure your data from being corrupted and ensure the long life of your IT systems.
-
Partner with Compliant Solution Providers
Many healthcare practitioners use digital methods to provide the best healthcare services possible. As a result, the need for digital healthcare solution providers has increased. However, with increasing data breaches, a thorough review of healthcare cloud security solution providers is one of the most critical security procedures healthcare businesses must implement. The HIPAA Omnibus Rule has strengthened prior requirements and provided specific definitions to improve confidentiality and security in data sharing with business partners.
Successive Digital Cloud Security Solutions for Healthcare is a compliant provider offering the best practices to protect sensitive healthcare data and enable healthcare organizations to go digital.
Trends You Must Know Around Healthcare Cloud Security
The healthcare industry is constantly experimenting with new trends and technologies; here are a few trends that healthcare businesses must know:
Increased Adoption of Hybrid Cloud Environments
Hybrid cloud adoption has increased from 25% to 42.5%, indicating greater confidence in this method. Why is that? Hybrid cloud services combine the robust security of private clouds with the scalability of public clouds. Thus, they provide flexible yet secure cloud storage in healthcare for handling the ever-increasing volumes of sensitive patient data. Hybrid cloud adoption is a perfect example of the leveraged benefits of cloud security for healthcare.
By adopting hybrid cloud environments, healthcare providers can store essential, sensitive information in a private cloud, giving them greater control over security protocols. At the same time, they can leverage the massive capabilities of a public cloud to perform less sensitive but resource-intensive operations such as data analytics or administrative functions. This strategy empowers your medical business to customize its cloud environment, instilling a sense of control and confidence in your security measures to satisfy unique demands and compliance.
Read this blog to know about- 9 Proven Tips for Cloud Backup and Recovery
AI and Machine Learning in Cloud Security
64% of executives have already included AI in their security systems, with another 29% actively considering its use. So, how do these advanced technologies protect your healthcare data from increasingly complex cyber-attacks?
AI and machine learning in healthcare can analyze massive amounts of data in real time, discovering unexpected patterns or potential hazards that a human team would take hours, if not days, to detect. This enables healthcare professionals to respond to security events more quickly and prevent them before they happen.
Hypothetically, if a healthcare worker clicks on a phishing email, putting the entire network in danger. ML algorithms can instantly detect this anomalous conduct, flagging it for prompt action or automatically prohibiting access. This speedy response distinguishes between a minor problem and a full-fledged data breach.
AI and ML in healthcare cloud security go beyond mere threat detection. They proactively assist in compliance with legislation, manage access controls, and even predict future security trends based on existing data. This proactive approach ensures compliance and puts the organization in control over potential security threats.
Emergence of Zero Trust Security Models
Gone are the days when security measures were only focused on establishing a solid perimeter to keep intruders out. The zero-trust model accepts that security threats can come from anywhere, including within your business. It’s like having an advanced security system installed at the hospital’s entrance and every door, window, and medication cabinet. Every user, device, and network flow is viewed as a possible risk and must be confirmed before accessing sensitive data.
Zero-trust models follow a comprehensive principle: check every access request, regardless of origin. This shifts the focus from blocking unwanted access to continuous monitoring and assessing the security posture of everything that interacts with your healthcare cloud environment. This method, which has quickly become an essential part of healthcare cloud security measures, ensures that your healthcare data is protected from all possible security threats, making you feel secure and confident in your data security.
Conclusion
Ensuring strong cloud security in healthcare is no easy task, but a well-protected and well-managed cloud infrastructure can secure your sensitive data. To keep up with the competition, your healthcare business must have streamlined operations, improved patient care, and a reputation. This all can be achieved with the digital transformation of your healthcare business. Collaboration with a reliable cloud consulting company can help secure your healthcare data and speed up the transformation.